- A sending device - Initiates an instruction to transmit data, instructions, information
- A communications device - Connects the sending device to a communications channel
- A communication channel - Transmission media on which the data, instructions, or information
- A communications device - Connects the sending device to a communications channel
- A receiving device - Accepts the transmission of data, instruction of information
Uses of computer communication
- Internet - A worldwide collection of networks that links millions of businesses, government agencies, educations, and individual
- Web - Worldwide collection of electronic documents on the internet that users access through Web browser.
- E-Mail - Or Electronic mail, is type of mail message that is sent through the network.
- Instant messaging - A Real-time internet communication service that notifies you when one or more people are online,then allows you to exchange messages, pictures, files, audio and video.
- Chat rooms - A Real-time typed in conversation that takes place on a computer connected to a network, that also allows you to exchange messages, pictures, files, audio and video.
- Newsgroup - Online areas in which user’s have written discussion about a particular subject.
- Internet telephony - A conversation takes place over the internet using a telephone connected to a desktop computer.
- FTP - Internet standard that permits or allows user to upload or download files.
- Web Folder - Known as HTTP server, allows users publish documents and other files.
- Video conferencing - Realtime meeting over two person, use the internet to transmit audio and video signal.
- Fax Machine or Computer fax/modem - Transmits and receives documents over the phone line.
Network Communications Standard
Data is processed in one of two ways: Analog or Digital. A computer, by contrast, is Digital Which means it can process data in two discrete states: Positive (ON or 1) Non-Positive (OFF or 0). The 1 and 0 represent the two digits used by the binary number system, this system is at the heart of digital computing.
Computer Network - A collection of computers and devices connected together via communications devices and transmission media.
Classifications of Network
 |
| Local Area Network |
 |
| Wireless LAN |
 |
| MAN Netwok |
 |
| WAN Network |
Network Architectures
Network Architecture - Is the design of computers, devices and media in a network.
 |
| Client Server Network |
- File Servers
- Domain Controller
- Internet proxy server
- Print server
- Cross-over network - Connect two computer using cross over utp cable. This type of connection does not require a network hub or a network switch.
- Null modem cable - A null modem cable connects to two standard serial ports for networking two computers together. Null modem cables enable direct data transfer with a minimum of setup required. A null modem cable differs from ordinary serial cables the same way as Ethernet crossover cables differ from ordinary Ethernet cables. Null modem cables reverse the transmit and receive lines on end to enable direct two-way communication. A null modem cable for PCs ordinarily follows the RS-232 standard and uses the same serial ports as RS-232 cables. An RS-232 null modem cable transfers data at the rate of 115 Kbps. The fastest null modem cable, based on RS-422, supports up to 450 Kbps.
Internet Peer-to-peer network (P2P) - Another type of peer-to-peer, called P2P, describes an internet network on which users access each other’s network harddisk and exchange files directly into the internet.
Network Topology
Network Topology - Is the physical topology of a network refers to the configuration of cables, computers, and other peripherals. Physical topology should not be confused with logical topology which is the method used to pass information between workstations. The following sections discuss the physical topologies used in networks and other related topics.
Main Types Physical Topologies
- Linear Bus Topology
- Star Topology
- Star-Wired Ring Topology
- Tree Topology
Linear Bus Topology - A linear bus topology consists of a main run of cable with a terminator at each end All nodes (file server, workstations, and peripherals) are connected to the linear cable. Ethernet and LocalTalk networks use a linear bus topology.
Advantages of a Linear Bus Topology
- Easy to connect a computer or peripheral to a linear bus.
- Requires less cable length than a star topology.
Disadvantages of a Linear Bus Topology
- Entire network shuts down if there is a break in the main cable.
- Terminators are required at both ends of the backbone cable.
- Difficult to identify the problem if the entire network shuts down.
- Not meant to be used as a stand-alone solution in a large building.
Star Topology - A star topology is designed with each node (file server, workstations, and peripherals) connected directly to a central network hub or concentrator.Data on a star network passes through the hub or concentrator before continuing to its destination. The hub or concentrator manages and controls all functions of the network. It also acts as a repeater for the data flow. This configuration is common with twisted pair cable; however, it can also be used with coaxial cable or fiber optic cable.
Advantages of a Star Topology
- Easy to install and wire.
- No disruptions to the network then connecting or removing devices.
- Easy to detect faults and to remove parts.
Disadvantages of a Star Topology
- Requires more cable length than a linear topology.
- If the hub or concentrator fails, nodes attached are disabled.
- More expensive than linear bus topologies because of the cost of the concentrators.
- The protocols used with star configurations are usually Ethernet or LocalTalk. Token Ring uses a similar topology, called the star-wired ring.
Star-Wired Ring - A star-wired ring topology may appear (externally) to be the same as a star topology. Internally, the MAU (multistation access unit) of a star-wired ring contains wiring that allows information to pass from one device to another in a circle or ring. The Token Ring protocol uses a star-wired ring topology.
Tree Topology - A tree topology combines characteristics of linear bus and star topologies. It consists of groups of star-configured workstations connected to a linear bus backbone cable (See fig. 4). Tree topologies allow for the expansion of an existing network, and enable schools to configure a network to meet their needs.
Advantages of a Tree Topology
- Point-to-point wiring for individual segments.
- Supported by several hardware and software vendors.
Disadvantages of a Tree Topology
- Overall length of each segment is limited by the type of cabling used.
- If the backbone line breaks, the entire segment goes down.
- More difficult to configure and wire than other topologies.
5-4-3 Rule - A consideration in setting up a tree topology using Ethernet protocol is the 5-4-3 rule. One aspect of the Ethernet protocol requires that a signal sent out on the network cable reach every part of the network within a specified length of time. Each concentrator or repeater that a signal goes through adds a small amount of time. This leads to the rule that between any two nodes on the network there can only be a maximum of 5 segments, connected through 4 repeaters/concentrators. In addition, only 3 of the segments may be populated (trunk) segments if they are made of coaxial cable. A populated segment is one which has one or more nodes attached to it . In Figure 4, the 5-4-3 rule is adhered to. The furthest two nodes on the network have 4 segments and 3 repeaters/concentrators between them. This rule does not apply to other network protocols or Ethernet networks where all fiber optic cabling or a combination of a fiber backbone with UTP cabling is used. If there is a combination of fiber optic backbone and UTP cabling, the rule is simply translated to 7-6-5 rule.
Considerations When Choosing a Topology
- Money - A linear bus network may be the least expensive way to install a network; you do not have to purchase concentrators.
- Length of cable needed - The linear bus network uses shorter lengths of cable.
- Future growth - With a star topology, expanding a network is easily done by adding another concentrator.
- Cable type - The most common cable in schools is unshielded twisted pair, which is most often used with star topologies.
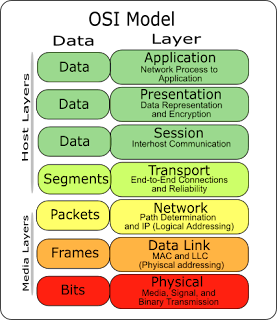
OSI Layer Model
The Open System Interconnection (OSI) reference model describes how information from a software application in one computer moves through a network medium to a software application in another computer. The OSI reference model is a conceptual model composed of seven layers, each specifying particular network functions. The model was developed by the International Organization for Standardization (ISO) in 1984, and it is now considered the primary architectural model for intercomputer communications. The OSI model divides the tasks involved with moving information between networked computers into seven smaller, more manageable task groups. A task or group of tasks is then assigned to each of the seven OSI layers. Each layer is reasonably self-contained so that the tasks assigned to each layer can be implemented independently. This enables the solutions offered by one layer to be updated without adversely affecting the other layers. The following list details the seven layers of the Open System Interconnection (OSI) reference model.
NETWORK PROTOCOL - A protocol is a set of rules that governs the communications between computers on a network. These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transfer.
Ethernet - The Ethernet protocol is by far the most widely used. Ethernet uses an access method called CSMA/CD (Carrier Sense Multiple Access/Collision Detection). This is a system where each computer listens to the cable before sending anything through the network. If the network is clear, the computer will transmit. If some other node is already transmitting on the cable, the computer will wait and try again when the line is clear. Sometimes, two computers attempt to transmit at the same instant. When this happens a collision occurs. Each computer then backs off and waits a random amount of time before attempting to retransmit. With this access method, it is normal to have collisions. However, the delay caused by collisions and retransmitting is very small and does not normally effect the speed of transmission on the network.
The Ethernet protocol allows for linear bus, star, or tree topologies. Data can be transmitted over wireless access points, twisted pair, coaxial, or fiber optic cable at a speed of 10 Mbps up to 1000 Mbps.
Fast Ethernet - To allow for an increased speed of transmission, the Ethernet protocol has developed a new standard that supports 100 Mbps. This is commonly called Fast Ethernet. Fast Ethernet requires the use of different, more expensive network concentrators/hubs and network interface cards. In addition, category 5 twisted pair or fiber optic cable is necessary. Fast Ethernet is becoming common in schools that have been recently wired.
Gigabit Ethernet - The most recent development in the Ethernet standard is a protocol that has a transmission speed of 1 Gbps. Gigabit Ethernet is primarily used for backbones on a network at this time. In the future, it will probably be used for workstation and server connections also. It can be used with both fiber optic cabling and copper. The 1000BaseTX, the copper cable used for Gigabit Ethernet, is expected to become the formal standard in 1999.
FDDI - Fiber Distributed Data Interface (FDDI) is a network protocol that is used primarily to interconnect two or more local area networks, often over large distances. The access method used by FDDI involves token-passing. FDDI uses a dual ring physical topology. Transmission normally occurs on one of the rings; however, if a break occurs, the system keeps information moving by automatically using portions of the second ring to create a new complete ring. A major advantage of FDDI is speed. It operates over fiber optic cable at 100 Mbps.
Types of Network Devices
Network card, network adapter, network interface controller (NIC), network interface card, or LAN adapter - is a computer hardware component designed to allow computers to communicate over a computer network. It is both an OSI layer 1 (physical layer) and layer 2 (data link layer) device, as it provides physical access to a networking medium and provides a low-level addressing system through the use of MAC addresses. It allows users to connect to each other either by using cables or wirelessly.
Network HUB - Ethernet hubs vary in the speed (network data rate or bandwidth) they support. Some years ago, Ethernet hubs offered only 10 Mbps rated speeds. Newer types of hubs offer 100 Mbps Ethernet. Some support both 10 Mbps and 100 Mbps (so-called dual-speed or 10/100 hubs). The number of ports an Ethernet hub supports also varies. Four- and five-port Ethernet hubs are most common in home networks, but eight- and 16-port hubs can be found in some home and small office environments. Older Ethernet hubs were relatively large in size and sometimes noisy as they contained built in fans for cooling the unit. Newer devices are much smaller, designed for mobility, and noiseless. Ethernet hubs operate as Layer 2 devices in the OSI model, the same as network switches.
- Network switches appear nearly identical to network hubs, operate at layer two (Data Link Layer) of the OSI model.
- Network switches generally contains more intelligence than a hub. Unlike hubs, network switches are capable of inspecting data packets as they are received, It determining the source and destination device of each packet, and forwarding them appropriately. By delivering messages only to the connected device intended, a network switch conserves network bandwidth and offers generally better performance than a hub.
- Ethernet network switches support either 10/100 Mbps Fast Ethernet or Gigabit Ethernet (10/100/1000) standards.
Difference Between a Hub and a Switch
- A switch is effectively a higher-performance alternative to a hub.
- Hubs operate using a broadcast model and switches operate using a virtual circuit model.
- When four computers are connected to a hub, for example, and two of those computers communicate with each other, hubs simply pass through all network traffic to each of the four computers.
- Switches, on the other hand, are capable of determining the destination of each individual traffic element (such as an Ethernet frame) and selectively forwarding data to the one computer that actually needs it. By generating less network traffic in delivering messages, a switch performs better than a hub on busy networks.
Routers
- Are physical devices that join multiple wired or wireless networks together. Technically, a wired or wireless router is a Layer 3 gateway, meaning that the wired/wireless router connects networks (as gateways do), and that the router operates at the network layer of the OSI model.
- Home networkers often use an Internet Protocol (IP) wired or wireless router, IP being the most common OSI network layer protocol.
- An IP router such as a DSL or cable modem broadband router joins the home's local area network (LAN) to the wide-area network (WAN) of the Internet.
- By maintaining configuration information in a piece of storage called the routing table, wired or wireless routers also have the ability to filter traffic, either incoming or outgoing, based on the IP addresses of senders and receivers.
- Some routers allow the home networker to update the routing table from a Web browser interface. Broadband routers combine the functions of a router with those of a network switch and a firewall in a single unit.
RJ45 (Registered Jack 45)
- A standard type of connector for network cables. RJ45 connectors are most commonly seen with Ethernet cables and networks.
- RJ45 connectors feature eight pins to which the wire strands of a cable interface electrically. Standard pinouts define the arrangement of the individual wires needed when attaching connectors to a cable.
- Several other kinds of connectors closely resemble RJ45 and can be easily confused for each other. The RJ-11 connectors used with telephone cables, for example, are only slightly smaller (narrower) than RJ-45 connectors.
CAT5 UTP (Unshielded Twisted Pair) Cable - The quality of UTP may vary from telephone-grade wire to extremely high-speed cable. The cable has four pairs of wires inside the jacket. Each pair is twisted with a different number of twists per inch to help eliminate interference from adjacent pairs and other electrical devices. The tighter the twisting, the higher the supported transmission rate and the greater the cost per foot. The EIA/TIA (Electronic Industry Association/Telecommunication Industry Association) has established standards of UTP and rated five categories of wire.
Network Cabling
Here is what the internals of the cable look like,Internal Cable Structure and Color Coding Inside the cable, there are 8 color coded wires. These wires are twisted into 4 pairs of wires, each pair has a common color theme. One wire in the pair being a solid or primarily solid colored wire and the other being a primarily white wire with a colored stripe (Sometimes cables won't have any color on the striped wire, the only way to tell which is which is to check which wire it is twisted around). Examples of the naming schemes used are: Orange (alternatively Orange/White) for the solid colored wire and White/Orange for the striped cable. The twists are extremely important. They are there to counteract noise and interference. It is important to wire according to a standard to get proper performance from the cable. The TIA/EIA-568-A specifies two wiring standards for an 8-position modular connector such as RJ45. The two wiring standards, T568A and T568B vary only in the arrangement of the colored pairs. Tom writes to say "...sources suggest using T568A cabling since T568B is the AT&T standard, but the US Government specifies T568A since it matches USOC cabling for pairs 1 & 2, which allows it to work for 1/2 line phones...". Your choice might be determined by the need to match existing wiring, jacks or personal preference, but you should maintain consistency. I've shown both below for straight through cabling and just T568B for cross over cabling.
About RJ45 Plugs and Jacks - The RJ45 plug is an 8-position modular connector that looks like a large phone plug. For braided/stranded wires, the connector has sharp pointed contacts that actually pierce the wire. For solid wires, the connector has fingers which cut through the insulation and make contact with the wire by grasping it from both sides. The connector is the weak point in an ethernet cable, choosing the wrong one will often cause grief later. If you just walk into a computer store, it's nearly impossible to tell what type of plug it is. You may be able to determine what type it is by crimping one without a cable. RJ45 jacks come in a variety styles intended for several different mounting options. The choice is one of requirements and preference. RJ45 jacks are designed to work only with solid cable. Most jacks come labeled with color codes for either T568A, T568B or both. Make sure you end up with the correct one.
Ethernet Cable Pin Outs
There are two basic cable pin outs. A straight through cable, which is used to connect to a hub or switch, and a cross over cable used to operate in a peer-to-peer fashion without a hub/switch. Generally all fixed wiring should be run as straight through. Some Ethernet interfaces can cross and un-cross a cable automatically as needed, a handy feature.
How to wire Ethernet Patch Cables
- Strip off about 2 inches of the cable sheath.
- Untwist the pairs - don't untwist them beyond what you have exposed, the more untwisted cable you have the worse the problems you can run into.
- Align the colored wires according to the diagrams above.
- Trim all the wires to the same length, about 1/2" to 3/4" left exposed from the sheath.
- Insert the wires into the RJ45 plug - make sure each wire is fully inserted to the front of the RJ45 plug and in the correct order. The sheath of the cable should extend into the RJ45 plug by about 1/2" and will be held in place by the crimp.
- Crimp the RJ45 plug with the crimper tool.
- Verify the wires ended up the right order and that the wires extend to the front of the RJ45 plug and make good contact with the metal contacts in the RJ45 plug
- Cut the cable to length - make sure it is more than long enough for your needs.
- Repeat the above steps for the second RJ45 plug.
How to wire fixed Ethernet Cables
- Run the full length of cable in place, from endpoint to endpoint, making sure to leave excess.
- At one end, cut the wire to length leaving enough length to work, but not too much excess.
- Strip off about 2 inches of the cable sheath.
- Align each of the colored wires according to the layout of the jack.
- Use the punch down tool to insert each wire into the jack.
- Repeat the above steps for the second RJ45 jack. If a cable tester is available, use it to verify the proper connectivity of the cable. That should be it, if your cable doesn't turn out, look closely at each end and see if you can find the problem. Often a wire ended up in the wrong place or one of the wires is making no contact or poor contact. Also double check the color coding to verify it is correct. If you see a mistake or problem, cut the end off and start again. A cable tester is invaluable at identifying and highlighting these issues.When sizing cables remember that an end to end connection should not extend more than 100m (~328ft). Try to minimize the cable length, the longer the cable becomes, the more it may affect performance. This is usually noticeable as a gradual decrease in speed and increase in latency.
CAT5 Cable - is an Ethernet network cable standard defined by the Electronic Industries Association and Telecommunications Industry Association (commonly known as EIA/TIA). CAT5 is the fifth generation of twisted pair Ethernet technology and the most popular of all twisted pair cables in use today.CAT5 cable contains four pairs of copper wire. It supports Fast Ethernet speeds (up to 100 Mbps). As with all other types of twisted pair EIA/TIA cabling, CAT5 cable runs are limited to a maximum recommended run length of 100m (328 feet). Although CAT5 cable usually contains four pairs of copper wire, Fast Ethernet communications only utilize two pairs. A newer specification for CAT5 cable - CAT5 enhanced (CAT5e) - supports networking at Gigabit Ethernet[ speeds (up to 1000 Mbps) over short distances by utilizing all four wire pairs, and it is backward-compatible with ordinary CAT5.Twisted pair cable like CAT5 comes in two main varieties, solid and stranded. Solid CAT5 cable supports longer length runs and works best in fixed wiring configurations like office buildings. Stranded CAT5 cable, on the other hand, is more pliable and better suited for shorter-distance, movable cabling such as on-the-fly patch cabling. Though newer cable technologies like CAT6 and CAT7 are in development, CAT5 / CAT5e Ethernet cable remains the popular choice for most wired local area networks (LANs), because Ethernet gear is both affordable and supports high speeds.
CAT6 Cable - is an Ethernet cable standard defined by the Electronic Industries Association and Telecommunications Industry Association (commonly known as EIA/TIA). CAT6 is the sixth generation of twisted pair Ethernet cabling. CAT6 cable contains four pairs of copper wire like the previous generation CAT5. Unlike CAT5, however, CAT6 fully utilizes all four pairs. CAT6 supports Gigabit Ethernet speeds up to 1 gigabit per second (Gbps) and supports communications at more than twice the speed of CAT5e, the other popular standard for Gigabit Ethernet cabling. An enhanced version of CAT6 called CAT6a supports up to 10 Gbps speeds.As with all other types of twisted pair EIA/TIA cabling, individual CAT6 cable runs are limited to a maximum recommended length of 100m (328 feet). Printing along the length of the cable sheath identifies it as CAT6.
Wireless access points (APs or WAPs) - are specially configured nodes on wireless local area networks (WLANs). Access points act as a central transmitter and receiver of WLAN radio signals. Access points used in home or small business networks are generally small, dedicated hardware devices featuring a built-in network adapter, antenna, and radio transmitter. Access points support Wi-Fi wireless communication standards. Although very small WLANs can function without access points in so-called "ad hoc" or peer-to-peer mode, access points support "infrastructure" mode. This mode bridges WLANs with a wired Ethernet LAN and also scales the network to support more clients. Older and base model access points allowed a maximum of only 10 or 20 clients; many newer access points support up to 255 clients.
Basic Internet Connection Procedure
Installing Phone Filters - You must install the included Phone Line Filters on every device (phones, fax machine, satellite receivers etc.) that is connected to the same line as your new DSL.
How to Installing DSL Modem
- Plug the included Phone Line Splitter into your Wall Jack. If you are going to be using another device (phone, fax machine, satellite receiver etc.) plug-in one of your Phone Line filters into the Splitter and then plug your phone into the filter. On the other side of the splitter hookup your DSL modem directly with the supplied phone cable. Be sure to plug it into the LINE or DSL port on the back of your modem.
- Make sure your computer is turned off.
- Take the supplied Ethernet cable and plug it into the LAN or ETHERNET port on the back of the modem. Plug the other end of the cable into the Ethernet port on the computer.
- Plug the supplied power cord into the modem and then into an available plug nearby. Once you plug-in the power supply, the modem will turn on automatically. If there is a switch on the back of the modem make sure to flip it to the ON position.
- Once the READY, SYNC/PPPoE or LINE light on the front of the modem stops blinking, turn your computer on and you will be ready to surf the internet.